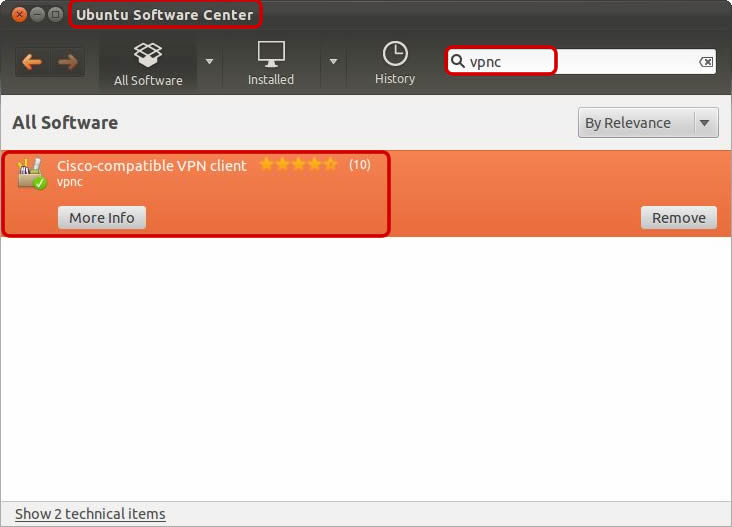
IPsec (Cisco/Juniper) VPN concentrator client. Contribute to streambinder/vpnc development by creating an account on GitHub. Jul 23, 2018 sudo apt-get install vpnc. Create and customize config: sudo nano /etc/vpnc/fritzbox.conf. IPSec gateway arpdggefuegr23723n.myfritz.net IPSec ID vpnuser IPSec secret TANrpS1y34hHHJGIS4 IKE Authmode psk Xauth username vpnuser Xauth password local port 0 DPD idle timeout (our side) 0. First test of the tunnel: sudo vpnc fritzbox.conf.
-->Syntax
Description
The Set-VpnConnectionIpsecConfiguration cmdlet sets the IPsec parameters of a VPN connection.The settings apply only to IKEv2 and L2TP VPN connections.
Examples
Example 1: Set the IPsec configuration for an IKEv2 tunnel
This example sets the IPsec configuration for a VPN connection using IKEv2.
The first command uses the Add-VpnConnection cmdlet to add a VPN connection on the server with the address 176.16.1.2.The cmdlet specifies an IKEv2 tunnel.
The second command uses the Set-VpnConnectionIPsecConfiguration cmdlet to set the configuration by using the ConnectionName parameter.The command also specifies values for the CipherTransformConstants, EncryptionMethod, IntegrityCheckMethod, and DHGroup parameters.
Example 2: Set the IPsec configuration for an L2TP tunnel
This example sets the IPsec configuration for an L2TP tunnel.
The first command uses Add-VpnConnection to add a VPN connection on the server with the address 176.16.1.2.The command also specifies an L2TP tunnel.
The second command uses Set-VpnConnectionIPsecConfiguration to set the configuration.The command also specifies values for the CipherTransformConstants, EncryptionMethod, IntegrityCheckMethod, and DHGroup parameters.
Example 3: Set the IPsec configuration for an IKEv2 tunnel with 128-bit data blocks
This example sets the IPsec configuration for an IKEv2 tunnel with authentication transform constants.
The first command uses Add-VpnConnection to add a VPN connection on the server with the address 176.16.1.2.The cmdlet specifies an IKEv2 tunnel.
The second command uses Set-VpnConnectionIPsecConfiguration to set the configuration.The command also specifies values for the CipherTransformConstants, EncryptionMethod, IntegrityCheckMethod, and DHGroup parameters, as well as specifying a value for the AuthenticationTransformConstants parameter.
Example 4: Set the IPsec configuration for an IKEv2 tunnel with 256-bit data blocks
This example sets the IPsec configuration for an IKEv2 tunnel, and specifies authentication transform constants.
The first command uses Add-VpnConnection to add a VPN connection on the server with the address 176.16.1.2.The cmdlet specifies an IKEv2 tunnel.
The second command uses Set-VpnConnectionIPsecConfiguration to set the configuration.The command also specifies values for the CipherTransformConstants, EncryptionMethod, IntegrityCheckMethod, and DHGroup parameters, as well as specifying a value for the AuthenticationTransformConstants parameter.
Parameters
Indicates that the VPN connection being modified is in the global phone book.
| Type: | SwitchParameter |
| Position: | Named |
| Default value: | None |
| Accept pipeline input: | False |
| Accept wildcard characters: | False |
Runs the cmdlet as a background job. Use this parameter to run commands that take a long time to complete.
| Type: | SwitchParameter |
| Position: | Named |
| Default value: | None |
| Accept pipeline input: | False |
| Accept wildcard characters: | False |
Specifies authentication header (AH) transform in the IPsec policy.For more information, see the Set-VpnServerIPsecConfiguration cmdlet.The acceptable values for this parameter are:
- MD596
- SHA196
- SHA256128
- GCMAES128
- GCMAES192
- GCMAES256
- None
| Type: | AuthenticationTransformConstants |
| Accepted values: | MD596, SHA196, SHA256128, GCMAES128, GCMAES192, GCMAES256, None |
| Position: | 2 |
| Default value: | None |
| Accept pipeline input: | True |
| Accept wildcard characters: | False |
Runs the cmdlet in a remote session or on a remote computer.Enter a computer name or a session object, such as the output of a New-CimSession or Get-CimSession cmdlet.The default is the current session on the local computer.
| Type: | CimSession[] |
| Aliases: | Session |
| Position: | Named |
| Default value: | None |
| Accept pipeline input: | False |
| Accept wildcard characters: | False |
Specifies Encapsulating Security Payload (ESP) cipher transform in the IPsec policy.Acceptable values for this parameter are:
- DES
- DES3
- AES128
- AES192
- AES256
- GCMAES128
- GCMAES192
- GCMAES256
- None
| Type: | CipherTransformConstants |
| Accepted values: | DES, DES3, AES128, AES192, AES256, GCMAES128, GCMAES192, GCMAES256, None |
| Position: | 3 |
| Default value: | None |
| Accept pipeline input: | True |
| Accept wildcard characters: | False |
Prompts you for confirmation before running the cmdlet.
| Type: | SwitchParameter |
| Aliases: | cf |
| Position: | Named |
| Default value: | False |
| Accept pipeline input: | False |
| Accept wildcard characters: | False |
Specifies the name of a VPN connection profile to modify.To view existing VPN connection profiles, use the Get-VpnConnection cmdlet.
| Type: | String |
| Aliases: | Name |
| Position: | 1 |
| Default value: | None |
| Accept pipeline input: | True |
| Accept wildcard characters: | False |
Specifies the Diffie-Hellman (DH) Group to use during IKE key exchanges.The acceptable values for this parameter are:
- None
- Group1
- Group2
- Group14
- ECP256
- ECP384
- Group24
| Type: | DHGroup |
| Accepted values: | None, Group1, Group2, Group14, ECP256, ECP384, Group24 |
| Position: | 4 |
| Default value: | None |
| Accept pipeline input: | True |
| Accept wildcard characters: | False |
Specifies the encryption method.The acceptable values for this parameter are:
- DES
- DES3
- AES128
- AES192
- AES256
- GCMAES128
- GCMAES256
| Type: | EncryptionMethod |
| Accepted values: | DES, DES3, AES128, AES192, AES256, GCMAES128, GCMAES256 |
| Position: | 5 |
| Default value: | None |
| Accept pipeline input: | True |
| Accept wildcard characters: | False |
Forces the command to run without asking for user confirmation.
| Type: | SwitchParameter |
| Position: | Named |
| Default value: | None |
| Accept pipeline input: | False |
| Accept wildcard characters: | False |
Specifies the integrity check method used to protect data from tampering.The acceptable values for this parameter are:
- MD5
- SHA1
- SHA256
- SHA384
| Type: | IntegrityCheckMethod |
| Accepted values: | MD5, SHA1, SHA256, SHA384 |
| Position: | 6 |
| Default value: | None |
| Accept pipeline input: | True |
| Accept wildcard characters: | False |
Returns an object representing the item with which you are working.By default, this cmdlet does not generate any output.If you specify this parameter, the cmdlet returns the VpnConnection object that contains the VpnConnection configuration settings.
| Type: | SwitchParameter |
| Position: | Named |
| Default value: | None |
| Accept pipeline input: | False |
| Accept wildcard characters: | False |
Specifies the Perfect Forwarding Secrecy (PFS) Group in the IPsec policy.The acceptable values for this parameter are:
- None
- PFS1
- PFS2
- PFS2048
- ECP256
- ECP384
- PFSMM
- PFS24
| Type: | PfsGroup |
| Accepted values: | None, PFS1, PFS2, PFS2048, ECP256, ECP384, PFSMM, PFS24 |
| Position: | 7 |
| Default value: | None |
| Accept pipeline input: | True |
| Accept wildcard characters: | False |
Indicates that the cmdlet sets the IPsec parameters to the default values.
| Type: | SwitchParameter |
| Position: | 2 |
| Default value: | None |
| Accept pipeline input: | False |
| Accept wildcard characters: | False |
Specifies the maximum number of concurrent operations that can be established to run the cmdlet.If this parameter is omitted or a value of 0 is entered, then Windows PowerShell® calculates an optimum throttle limit for the cmdlet based on the number of CIM cmdlets that are running on the computer.The throttle limit applies only to the current cmdlet, not to the session or to the computer.
| Type: | Int32 |
| Position: | Named |
| Default value: | None |
| Accept pipeline input: | False |
| Accept wildcard characters: | False |
Shows what would happen if the cmdlet runs.The cmdlet is not run.
| Type: | SwitchParameter |
| Aliases: | wi |
| Position: | Named |
| Default value: | False |
| Accept pipeline input: | False |
| Accept wildcard characters: | False |
Outputs
Related Links
VPN setup in Ubuntu – General introduction
VPN (Virtual Private Network) lets you establish a secure connection over the non-secure Internet, e.g. from a notebook to an office server.
Getting a VPN to work requires general knowledge on networks, and it may require some specific knowledge on routers, firewalls and VPN protocols.
In order to use VPN on Ubuntu, you need to make sure that support for the required VPN protocol is installed. Several VPN protocols exist:
PPTP (Microsoft VPN)
Cisco VPN
Vpn Ipsec Service Android
OpenVPN
IPSec VPN
Not covered on this page, so far
Usage
- Click on the network-manager in the system tray
Choose VPN Connections -> Configure VPN
- Click Add
You might have to restart the network-manager to get the added VPN connection on the list (killall nm-applet; nm-applet &)
- Now the VPN connection should be shown in the network-manager
VPN setup in Kubuntu Feisty (7.04)
You have to install the additional package
Please refer to WifiDocs/NetworkManager under VPN support for more information.
VPN setup using the command line
Run the following:
Create file /etc/ppp/peers/YOUR_COMPANY with this content: Wipeout command autocad.
Add to /etc/ppp/chap-secrets:
Create file /etc/ppp/ip-up.d/add-subnet with content similar to:
In the above line, adjust subnet values (192.168.100.0/24) if needed
Then run:
- Connect to VPN: sudo pon YOUR_COMPANY To disconnect, press Ctrl+C or close the terminal.
Vpnc Ipsec 3
- If you do not want to see VPN connection debug output, in file /etc/ppp/peers/YOUR_COMPANY delete 3 lines: debug nodetach logfd 2
In this case, “pon YOUR_COMPANY” will run as a background process. Use “poff YOUR_COMPANY” to disconnect.
Vpnc Ipsec.conf
VPN setup in Ubuntu 8.10
I stole these instructions written by mgmiller from http://ubuntuforums.org/showpost.php?p=7089396&postcount=196. This is for connecting to a Microsoft VPN.
- You need to install 2 packages:
- network-manager-pptp
- pptp-linux
- input the IP address of the target computer.
- input your user name. Leave all else blank, unless you are tunneling to a domain, then enter the domain name where indicated.
- hit Advanced button.
- UNcheck PAP (because PAP means to allow unsecured passage - this is the source of 'no shared shared secrets')
- Check CHAP, MSCHAP and MSCHAPv2.
- Check Use Point-to-point encryption (MPPE)
- Select 128-bit (most secure).
- Check Allow stateful encryption.
Vpnc Ipsec Target Network
VPN setup in Ubuntu 9.04
I could not get any VPN working on 9.04. There appears to be some bugs in the configuration tools, you may be able to get things to work via the command line.
VPN setup in Ubuntu 9.10
The following instructions were originally written by sweisler at http://ubuntuforums.org/showpost.php?p=8261958&postcount=6. They have been additionally tested for PPTP to an MS VPN:
- Here's a synopsis of my VPN setups. I have proven this to work on both x86 and x64 for all 3 VPN types. Important note/disclaimer: I tested these configurations on VMware Workstation 7 VM's and a Dell Vostro 220. All installations were fresh installs, not upgrades. Also, please notice that I detail what type of firewall/VPN I am connecting to for each VPN type. There are so many variations on these VPN implementations that it is extremely difficult to generalize a known-good configuration for each.
- Install various VPN components
- PPTP
- pptp-linux
- network-manager-pptp
- vpnc
- network-manager-vpnc
c. OpenConnect
- openconnect
- network-manager-openconnect
- PPTP
- Reboot
- PPTP VPN Configuration - This setup works for connecting to ISA 2004/2006 PPTP VPNs. It should work for connecting to MS PPTP VPN implementations in general. I can't speak for other PPTP VPN implementations.
- Create new PPTP connection
- VPN Tab Settings
- Set Connection name
- Set Gateway
- Set username (for domain-based user accounts, use domainusername)
- DO NOT SET PASSWORD
- DO NOT SET NT DOMAIN
- PPTP Advanced Options (Advanced button)
- uncheck all auth methods EXCEPT MSCHAPv2
- check 'Use Point-to-Point encryption (MPPE)'
- leave Security set at 'All Available (Default)'
- trying to force encryption level causes this option to become unset
- check 'Allow stateful inspection'
- uncheck 'Allow BSD Data Compression'
- uncheck 'Allow Deflate Data Compression'
- uncheck 'Use TCP Header Compression'
- uncheck 'Send PPP Echo Packets' (although connection works either checked or unchecked)
- save configuration
- enter password in login box
- DO NOT check either password save box at this time
- once connection establishes, verify remote connectivity - ping, rdp, ssh, etc.
- disconnect VPN session
- enter password in login box
- check both password save option boxes
- once again verify remote connectivity
- disconnect VPN session
- VPN session should automatically connect using saved auth credentials
- Create new PPTP connection
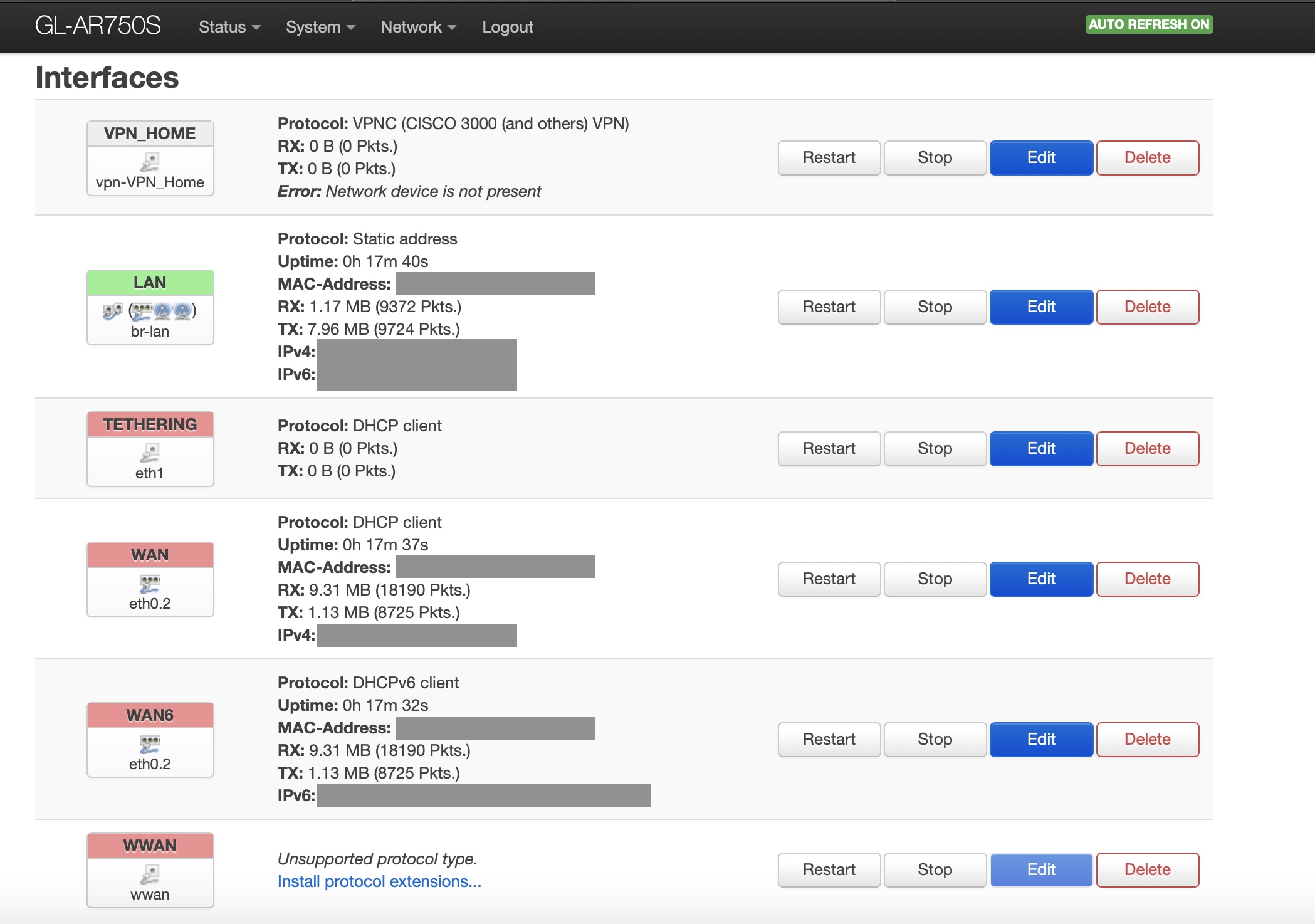
- VPNC VPN Configuration - This setup works connecting to an ASA5510 - software version 8.2(1). I didn't have any other Cisco devices to test against.
- Create new VPNC connection
- set connection name
- set Gateway
- set Group Name
- set User Password to 'Saved' and enter password
- set Group Password to 'Saved' and enter password
- set username
- set domain (if applicable)
- leave Encryption Method at 'Secure (Default)'
- set NAT traversal to 'NAT-T'
- save configuration
- open VPNC connection
- if prompted, select 'Always Allow' if you want connection to be automatic
- verify remote connectivity - ping, rdp, ssh, etc.
- disconnect VPN session
- open VPNC connection - session should automatically connect
- Create new VPNC connection
OpenConnect VPN Configuration - This setup works connecting to an ASA5510 - software version 8.2(1). I didn't have any other Cisco devices to test against.
Armies of exigo maps download. Create new OpenConnect connection
- set connection name
- set Gateway
- set Authentication type to 'Password/SecurID'
no need to set username, OpenConnect won't store it yet
- save configuration
- open VPN connection
- check 'Automatically start connecting next time'
- click Close
- you will get the 'No Valid VPN Secrets' VPN failure message
- open VPN connection
- accept certificate (if prompted)
- change Group (if necessary)
- enter username (may need to be domainusername)
- enter password
- click Login
- if VPN connection fails, see note below
- verify remote connectivity - ping, rdp, ssh, etc.
- disconnect session
- open VPN connection
- enter password
- session should connect
Note: If you get the 'Login Failed' message, cancel and wait 15-30 minutes before attempting to connect again. Also, I ended up having to use the NT style domainusername pair for authentication, even though a Cisco AnyConnect client connecting to the same ASA only requires username.
More Detail: OpenConnect has been brutal to get connected. I got failed attempt after failed attempt. When I checked the NPS (IAS) log and the Security Event log on the W2K8 domain controller, I could see my user account authenticating properly via RADIUS from the ASA. Yet the OpenConnect client came back with a 'Login Failed' message. I'm not an ASA expert, so I have no idea what to check in the ASA configuration to troubleshoot this problem, other than the basic AAA configuration. But I believe the problem lies in the ASA configuration because when I get the OpenConnect 'Login Failed' message, the AnyConnect client from my Windows laptop fails as well. I think it may be a ridiculously short timeout or max failure setting. Whatever the issue is, I have to wait for some length of time (~15-30 minutes) for whatever the problem is to reset.
However, once I finally get the OpenConnect client to successfully connect, it worked from then on. (Just don't mess with the connection configuration, or you will get to go thru this whole process again.)
VPN setup in Ubuntu 10.04
Ubuntu 10.04 comes preinstalled with VPN support.
This features is available under the networks connections tab.
VPN (last edited 2015-05-21 10:52:58 by waldyrious)
