With ever increasing network congestion, having the tools to optimize your important business applications is becoming increasingly important.
- Network -.zoom.us ( it contains all the zoom IP addresses and is populated by the XG. Services - ZOOM special using the list of ports from the zoom site. I added ICMP because I found which is a bit concerning that ICMP was allowed out my firewall rule even though it was not on the allowed list.
- The LSE has a Zoom licence for all School staff and students. Below is a quick guide on how to install and start Zoom for the first time if you are LSE staff or an LSE student. Non LSE members can sign up for a free Zoom account and download the client from the Zoom website.
In this third in a series of articles on making the most of the great new features in XG Firewall v18, we’re going to focus on the tools available to you to optimize your important business application traffic using the new Xstream Network Flow FastPath and the new SD-WAN Policy Based Routing options.
Xstream FastPath Application Acceleration
In our last two articles, we covered the Xstream architecture and the new DPI engine as well as the new TLS Inspection in XG Firewall v18. The Network Flow FastPath is another key component of the new Xstream architecture and provides application acceleration for trusted traffic.
The Network Flow FastPath can direct trusted traffic that doesn’t require security scanning into the fast lane through the system. This not only minimizes latency and accelerates that application traffic through the firewall, it also has the added benefit of not engaging the DPI engine and TLS inspection resources for traffic that doesn’t require inspection.
Sophos Support Plans Our support plans range from basic technical support to options including direct access to senior support engineers and customized delivery. Receive Training As a Sophos Customer, you can attend our courses and webinars to stay up to date. Applies to: Sophos Home Premium (Windows and Mac) Webcam protection (available on Windows and Mac) is a Sophos Home feature that alerts you of unwanted use of your webcam. This feature is enabled by default. Mic protection (available on Mac only) is a Sophos Home feature that alerts you of unwanted use of your microphone. This feature is enabled by default. Controlled applications are programs, such as VoIP, IM, P2P and games, that can be blocked or allowed for different groups of computers, depending on productivity or security concerns.
This frees up those resources for traffic that actually needs it – creating added performance headroom in the process.
How it works
Initially, all traffic flows are processed by the Firewall stack and passed to the DPI engine for further identification. Once an application traffic flow is determined to be “trusted”, the Network Flow FastPath is directed to handle the packet flow directly and shuttle the packets through on the FastPath, bypassing the DPI engine.
Traffic can be accelerated onto the Network Flow FastPath in two ways:
- Automatically: If the application matches a Server Name Indication (SNI) from SophosLabs for traffic that is considered trustworthy and tamper proof such as video and audio streaming services (Netflix, Spotify, Pandora, etc.), secure updates fetched directly from within the application (from Microsoft, Apple, Adobe, Sophos, etc.) or VoIP and other streaming protocols (such as SIP, FIX, RDP, etc.)
- Policy: If there is a firewall rule associated with that specific application traffic that accelerates it onto the FastPath by not flagging it for security scanning.
You might be wondering, when would it make sense to accelerate application traffic on the FastPath, or in other words, what can be trusted? Traffic such as streaming media that is not active code-based is a perfect example of traffic that can be trusted.
Due to the streaming structure of the traffic and how it’s reassembled for playback, it’s not possible to inject malware into this kind of traffic flow making it an ideal candidate for FastPath acceleration. This type of traffic includes all popular streaming services such as Netflix and Spotify, but also VoIP and collaboration applications such as Zoom, GotoMeeting, Skype for Business, Microsoft Teams Calls, and others.
And of course, these communication and collaboration applications are among the most important in any business, which makes them ideal for FastPath acceleration.
Applications that enable users to download updates or files, are NOT good candidates for FastPath acceleration as files can obviously contain active code and be malicious. In general, in the interest of security, never create a FastPath rule for general web browsing or file sharing sites or applications.
Firewall Rules in XG Firewall v18
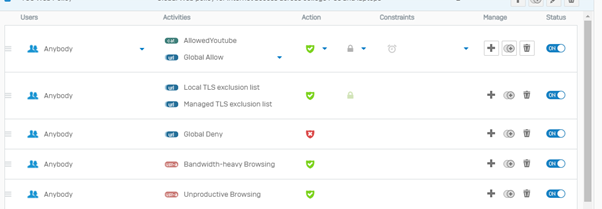
Firewall rules in XG Firewall v18 are very similar in their construction to previous releases, making migrations easy. This video provides a great in-depth look at firewall and NAT rule configuration in XG Firewall v18:
We will cover NAT rules in a future article in this series but today, let’s review how to create a firewall rule to accelerate trusted traffic on the FastPath. It couldn’t be more straightforward and intuitive: simply identify the destination application networks (FQDNs) or services…
And select “None” for Security Features and do not select any of the check boxes. This will ensure that traffic will be accelerated on the FastPath and not redirected through the DPI engine for unnecessary security scanning.
Then check that FastPath acceleration is enabled under Advanced threat > Advanced threat protection as shown below (it should be set by default). It’s that easy!
Application SD-WAN Policy Based Routing
Another new and improved capability in XG Firewall v18 is SD-WAN Policy Based Routing (PBR). Just as you want your important business application’s path through the firewall optimized and accelerated on the FastPath, you may also want to ensure your application’s path to the cloud or a branch office is similarly optimized. That’s where SD-WAN PBR comes in.
XG Firewall v18 adds user, group, and application-based traffic selection criteria to XG Firewall’s SD-WAN routing configuration. This allows you to route important business application traffic out a preferred ISP WAN link or a branch office VPN connection while less important traffic utilizes a different route.
This video provides a great overview of how to take advantage of the new SD-WAN PBR capabilities in XG Firewall v18 for application optimization, and SD-WAN routing.
Synchronized SD-WAN
XG Firewall v18 has evolved SD-WAN further with the introduction of Synchronized SD-WAN, a new Sophos Synchronized Security feature that offers additional benefits with SD-WAN application routing. Synchronized SD-WAN leverages the added clarity and reliability of application identification that comes with the sharing of Synchronized Application Control information between Sophos-managed endpoints and XG Firewall.
Synchronized Application Control can positively identify 100% of all networked applications, including evasive, encrypted, obscure, and custom applications and now these previously unidentified applications can also be added to SD-WAN routing policies. This provides a level of application routing control and reliability that other firewalls can’t match.
Here’s a summary of the resources available to help you make the most of the new features in XG Firewall v18, including application FastPath acceleration and SD-WAN Policy Routing:
If you’re new to Sophos XG Firewall, learn more about the great benefits and features XG Firewall can deliver to your network.
Sophos Zoom Udp Flood
The annual Pwn2Own contest features live hacking where top cybersecurity researchers duke it out under time pressure for huge cash prizes.
Sophos Zoom Background
Their quest: to prove that the exploits they claim to have discovered really do work under real-life conditions.
Indeed, Pwn2Own is a bug bounty program with a twist.
The end result is still responsible disclosure, where the affected vendor gets a chance to fix any flaws before they are made public, but the bug hunters don’t just submit their bug descriptions with a list of instructions for the vendor to follow and investigate.
The competitors are faced with a standardised, patched, vanilla configuration of the system they’re targeting, set up for them on hardware they didn’t choose theselves, and they have just 20 minutes in which to complete their attack during the competition.
That means there is very little time to adjust, adapt, rethink and rewrite code during the timed part of the event itself, so this really is a showcase for meticulous research, scrupulous preparation, careful rehearsal…
…mixed with a dash of je ne sais quoi and a dose of plain old luck.
The “plain old luck” factor exists because the participants do their demonstrations one after another over three days, with the order chosen randomly just before the competition starts.
If two teams show up with the same exploit, and both of those exploits succeed within the allotted time, then the winner isn’t the one who can prove they found it first during their research phase, but the one who just happened to get the earlier demonstration slot in the draw.
Clearly, the earlier the slot you draw, the less likely you are to get scooped by someone else who just happened to have found the same bug as you.
Greetz from Texas
Traditionally, the North American Pwn2Own event has taken place alongside the annual CanSecWest security conference held in Vancouver, Canada, but this year the official host city was Austin, Texas.
For obvious reasons, the actual hacking teams were distributed all over the world, rather than all travelling to meet in one place.
The full results for 2021 can be found on the Pwn2Own blog, including those who tried but failed, or those who tried but didn’t win any money because some part of their exploit chain was already known.
In some cases, competitors lost out because their exploits had been reported to the vendor before the competition by someone else, but not yet publicly disclosed; in other cases, they lost out simply through the bad luck of drawing a later slot in the competition than other participants who had brought along and exploited the same bugs.
We’ve listed the money-winning entries below – note that this year’s prize money totalled a very healthy $1.21 million!
The prize hierarchy looked like this:
- $200k for code execution on a server or messaging platform
- $100k for code execution via a browser
- $40k for breaking out of a virtualised guest OS into the host OS
- $40k for “getting root” (more properly, SYSTEM) on Windows 10
- $30k for “getting root” on Linux
In case you are wondering, EoP below is short for elevation of privilege, which means exactly what it says: it doesn’t get you into a system in the first place, but it does gets you up to superpower level once you’re in.
Interestingly, there was a tenth product that was attacked in the competition, but that doesn’t show up in the list above because it remained unpwned within the allotted time: Oracle’s VirtualBox virtualisation software.
See you next year!
Congratulations to everyone who took part…
…and good news for all the rest of us, because all the bugs that were painstakingly uncovered, understood and used in the attacks above – and note that many attacks required a number of different exploits to be unleashed in a specfic sequence – will now all be fixed.
To learn more about vulnerabilities and how attackers chain them together for more devastating results, listen to our Understanding Vulnerabilities podcast below:
LISTEN NOW – UNDERSTANDING VULNERABILITIES
Podcast originally recorded in 2010. You can also listen directly on Soundcloud.
